Cross Account Access
To achieve cross account access, and allow an AWS IAM Identitiy from Account A to access AWS resources in account B (S3 resource in our case) two conditions must be met:
-
The IAM Identity owner account A should give permission X on the S3 resource in account B.
In File Access Manager this permission will appear as X-ByTrustedCrossAccount
-
The S3 resource owner account B should give permission X on the resource to the IAM Identity from account A.
In File Access Manager this permission will appear as X-ByTrustingCrossAccount.
Permission X will be affective only if both permissions are granted to the user / group on the resource. Otherwise, the user / group will not be allowed to perform X on this resource.
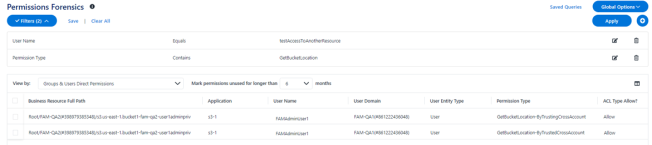
In the example above, the user “FAMAdminUser1” from account “FA-QA1” has both “GetBucketLocation-ByTrustingCrossAccount” and “GetBucketLocation-ByTrustedCrossAccount” permission on bucket “bucket1-fam-qa2-user1adminpriv” from account “FAM-QA2”.