Active Directory Integration with AWS
Active Directory has the ability to be integrated with AWS environments and allow users to use their already established login credentials, manage their user identities outside of AWS, and give these external user identities permissions to use AWS resources in their account.
When integrating Active Directory to AWS, the AWS S3 permissions needs to be mapped to the Active Directory users and groups by using an Identity Provider (IdP).
We support AWS 'SAML' and 'OpenID Connect' IdPs in case this is done in one of the following two ways:
-
An internal configuration inside the IDP. This would be supported by using a File Access Manager data source and would include a mapping file (Excel, CSV, etc.) that the client needs to provide and maintain.
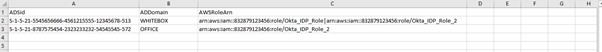
-
Using Active Directory group naming configuration. This method is ideal in case the client's IDP supports it and if the client created these groups.
Example: Active Directory group name – ad-aws-int-test1#Okta_IDP_Role_2#832879285990
This is the Active Directory group name template: [some name]#[role name]#[account id].
The user configures (in File Access Manager) the regular expression (regex)
Example: S+\#(?<rolename>[\w\-]+)\#(?<accountid>\d+)$. We then know to use this expression to extract the IAM Role name and the AWS account ID from the Active Directory group name and do the mapping.