Credential Provider Secret Path Expressions
Revised Date: 14 August 2025
Use the path expressions on this page to implement your configured credential providers into your source configurations.
Generic Format
Specific secret path expressions vary for each individual credential provider. The generic format of a secret path can be expressed as follows:
secrets://{vault_name}/{URI_Path_to_secret}/{secretKey}?version={versionnumber}
Important
The provided example has four parts to it, each highlighted with curly braces ({ }). Each part needs to be URI-encoded separately. SailPoint does not support complete URI encoding.
Secret Path Expressions by Credential Provider
The list is divided by the credential provider, and the secret path expressions they support are listed below them.
For information on how to configure the AWS Secret Manager credential provider, refer to AWS Secrets Manager.
Path syntax: {Secret ARN}/{secretKey}
For example:
Before Encoding
-
Using Secret ARN :
secrets://aws-vault/arn:aws:secretsmanager:us-east-1:441113549707:secret:orgName/cred/applicationName/directoryName/username
Important
The URL path should always start with the prefix, secrets://. Each attribute in the URL path must be URL-encoded. Each URL attribute in the path is case-sensitive.
After Encoding
After you encode the URL path, it should appear as follows:
-
Using Secret ARN :
secrets://aws-vault/arn%3Aaws%3Asecretsmanager%3Aus-east-1%3A441113549707%3Asecret%3AorgName%2Fcred%2FapplicationName%2FdirectoryName/username
The following is an explanation of the attributes of this URL:
-
Aws-vault– Configured Credential Provider in the Credential Provider Section -
arn:aws:secretsmanager:us-east-1:441113549707:secret:orgName/cred/applicationName/directoryName– Secret Path ARN -
username– Secret Key which needs to be fetched from the AWS secrets manager.
Tip
Use urlencoder.org to encode your URL attributes.
Path syntax: {Secret ARN}/{secretKey}
For example:
Before Encoding
-
Using Secret ARN :
secrets://aws-vault/arn:aws:secretsmanager:us-east-1:441113549707:secret:orgName/cred/applicationName/directoryName/password
Important
The URL path should always start with the prefix, secrets://. Each attribute in the URL path must be URL-encoded. Each URL attribute in the path is case-sensitive
After Encoding
After you encode the URL path, it should appear as follows:
-
Using Secret ARN :
secrets://aws-vault/arn%3Aaws%3Asecretsmanager%3Aus-east-1%3A441113549707%3Asecret%3AorgName%2Fcred%2FapplicationName%2FdirectoryName/password
The following is an explanation of the components of this URL:
-
Aws-vault– Configured Credential Provider in the Credential Provider Section -
arn:aws:secretsmanager:us-east-1:441113549707:secret:orgName/cred/applicationName/directoryName– Secret Path ARN -
password– Secret Key which needs to be fetched from the AWS secrets manager.
Tip
Use urlencoder.org to encode your URL attributes.
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://aws-vault/arn%3Aaws%3Asecretsmanager%3Aus-east-1%3A441113549707%3Asecret%3AorgName%2Fcred%2FapplicationName%2FdirectoryName/password?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
localadministrator, but the complete value required by the secret field islocaladminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://aws-vault/arn:aws:secretsmanager:us-east-1:441113549707:secret:orgName/cred/applicationName/directoryName/password?suffix=%40sp.com
-
To add a prefix and suffix –
?prefix=<prefix>&suffix=<suffix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdmin@sp.comthen the secret path expression will be as follows to add the required prefix:secrets://aws-vault/arn:aws:secretsmanager:us-east-1:441113549707:secret:orgName/cred/applicationName/directoryName/password?prefix=DomainOne%5C&suffix=%40sp.com
Important
All input parameters must be encoded.
Standard format for credential path
secrets://{vault-name}/{secret ARN}/{secretKey}?prefix=someValue&suffix=someValue2&versionId=123&versionStage=PREVIOUS
Important
Prefix, suffix, versionId and versionStage are optional.
The AWS Secrets Manager has provision to store secrets in two ways:
-
In Key value / JSON / Map format
-
Plain text format.
Note
For the secrets which are stored in plain text format, there is no need to provide the “secret key” in the credential path.
For example:
Before Encoding
-
Using Secret ARN :
secrets://aws-vault/arn:aws:secretsmanager:us-east-1:441113549707:secret:orgName/cred/applicationName/directoryName
Important
The URL path should always start with the prefix, secrets://. Each attribute in the URL path must be URL-encoded. Each URL attribute in the path is case-sensitive
After Encoding
After you encode the URL path, it should appear as follows:
-
Using Secret ARN :
secrets://aws-vault/arn%3Aaws%3Asecretsmanager%3Aus-east-1%3A441113549707%3Asecret%3AorgName%2Fcred%2FapplicationName%2FdirectoryName
Other Query Parameters
-
versionId – The unique identifier of the version of the secret to retrieve. If you include both this parameter and
VersionStage, the two parameters must refer to the same secret version. If you don't specify both theVersionStageandVersionId, then Secrets Manager returns theAWSCURRENTversion.Example :
secrets://aws-vault/arn%3Aaws%3Asecretsmanager%3Aus-east-1%3A441113549707%3Asecret%3AorgName%2Fcred%2FapplicationName%2FdirectoryName/password?versionId=123
-
versionStage – The staging label of the version of the secret to retrieve.
Secrets Manager uses staging labels to keep track of different versions during the rotation process. If you include both this parameter and
VersionId, the two parameters must refer to the same secret version. If you don't specify bothVersionStageandVersionId, Secrets Manager returns theAWSCURRENTversion.Example :
secrets://aws-vault/arn%3Aaws%3Asecretsmanager%3Aus-east-1%3A441113549707%3Asecret%3AorgName%2Fcred%2FapplicationName%2FdirectoryName/password?versionStage=AWSCURRENT
-
versionId and versionStage – If you include both the parameters
VersionStageandVersionId, the two parameters must refer to the same secret version. If you don't specify both theVersionStageandVersionId, Secrets Manager returns theAWSCURRENTversion.Example :
secrets://aws-vault/arn%3Aaws%3Asecretsmanager%3Aus-east-1%3A441113549707%3Asecret%3AorgName%2Fcred%2FapplicationName%2FdirectoryName/password?versionId=123&versionStage=AWSCURRENT
For information on how to configure the AWS Secret Manager credential provider, refer to Azure Key Vault.
Note
The reference examples provided on this page are for Secrets; similarly, follow the same approach for Keys and Certificates.
Before Encoding
-
Using Secret ARN:
secrets://azure-key-vault/https://jubileecpkeyvault.vault.azure.net/keys/HarshalFirstKey/value
Note
It is recommended to omit the version ID from secret, key, or certificate identifiers to always fetch the latest value.
Example: The secret identifier below includes a version ID:
https://jubileecpkeyvault.vault.azure.net/secrets/HarshalFirstKey/e5a9dd5cc1284a4caa5bef8cd733feab
The recommended approach is to omit the version ID from the identifier, ensuring that the latest value is always retrieved:
https://jubileecpkeyvault.vault.azure.net/secrets/HarshalFirstKey
Important
The URL path should always start with the prefix, secrets://. Each attribute in the URL path must be URL-encoded. Each URL attribute in the path is case-sensitive.
After Encoding
After you encode the URL path, it should appear as follows:
-
Using Secret ARN:
secrets://azure-key-vault/https%3A%2F%2Fjubileecpkeyvault.vault.azure.net%2Fkeys%2FHarshalFirstKey/value
The following is an explanation of the attributes of this URL:
-
Azure-key-vault– Configured Credential Provider on ISC. -
https%3A%2F%2Fjubileecpkeyvault.vault.azure.net%2Fkeys%2FHarshalFirstKey– Secret Identifier of the secret. -
value– The name of the secret which needs to be fetched from the JSON response.
Use urlencoder.org to encode your URL attributes.
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://azure-key-vault/https%3A%2F%2Fjubileecpkeyvault.vault.azure.net%2Fkeys%2FHarshalFirstKey/value?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
localadministrator, but the complete value required by the secret field islocaladminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://azure-key-vault/https%3A%2F%2Fjubileecpkeyvault.vault.azure.net%2Fkeys%2FHarshalFirstKey/value?suffix=%40sp.com
-
To add a prefix and suffix –
?prefix=<prefix>&suffix=<suffix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdmin@sp.comthen the secret path expression will be as follows to add the required prefix and suffix:secrets://azure-key-vault/https%3A%2F%2Fjubileecpkeyvault.vault.azure.net%2Fkeys%2FHarshalFirstKey/value?prefix=DomainOne%5C&suffix=%40sp.com
Important
All input parameters must be encoded.
Standard format for credential path
secrets://{credentialpprovider-source}/{secretidentifier}/{secretKey}?prefix=someValue&suffix=someValue2
Important
Prefix and Suffix are optional.
For information on how to configure the BeyondTrust Password Safe Cloud (Secrets Management) credential provider, refer to BeyondTrust Password Safe Cloud (Secrets Management).
Secret URL syntax:
secrets://{CredentialProviderName}/{SecretURL}
The following is an explanation of the attributes of this URL:
-
CredentialProviderName– The name of the credential provider source configured in ISC. -
SecretURL– A query string that uniquely identifies the secret within BeyondTrust Password Safe. It specifies the managed system and the managed account within that system. The format of the SecretURL is as follows:systemName={nameOfManagedSystem}&accountName={nameOfManagedAccount}
Important
-
CredentialProviderNameandSecretURLmust be URL-encoded individually before constructing the final secret path expression. -
systemNameandaccountNameare reserved keywords in the SecretURL format and must not be used as part of the values fornameOfManagedSystemornameOfManagedAccount.
Tip
Use urlencoder.org to encode your URL attributes.
Before Encoding
secrets://BeyondTrust Password Safe/systemName=Microsoft Entra ID&accountName=user@company.onmicrosoft.com
After Encoding
secrets://BeyondTrust%20Password%20Safe/systemName%3DMicrosoft%20Entra%20ID%26accountName%3Duser%40company.onmicrosoft.com
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
Secure#456, but the complete value required by the secret field isapp1-dev@Secure#456then the secret path expression will be as follows to add the required prefix:secrets://BeyondTrust%20Password%20Safe/systemName%3DMicrosoft%20Entra%20ID%26accountName%3Duser%40company.onmicrosoft.com?prefix=app1-dev%40
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
app1-dev, but the complete value required by the secret field isapp1-dev@Secure#456then the secret path expression will be as follows to add the required suffix:secrets://BeyondTrust%20Password%20Safe/systemName%3DMicrosoft%20Entra%20ID%26accountName%3Duser%40company.onmicrosoft.com?suffix=%40Secure%23456
For information on how to configure the BeyondTrust Password Safe On-Premise (Secrets Management) credential provider, refer to BeyondTrust Password Safe On-Premise (Secrets Manager).
Secret URL syntax:
secrets://{CredentialProviderName}/{SecretURL}
The following is an explanation of the attributes of this URL:
-
CredentialProviderName– The name of the credential provider source configured in ISC. -
SecretURL– A query string that uniquely identifies the secret within BeyondTrust Password Safe. It specifies the managed system and the managed account within that system. The format of the SecretURL is as follows:systemName={nameOfManagedSystem}&accountName={nameOfManagedAccount}
Important
-
CredentialProviderNameandSecretURLmust be URL-encoded individually before constructing the final secret path expression. -
systemNameandaccountNameare reserved keywords in the SecretURL format and must not be used as part of the values fornameOfManagedSystemornameOfManagedAccount.
Tip
Use urlencoder.org to encode your URL attributes.
Before Encoding
secrets://BeyondTrust Password Safe/systemName=Microsoft Entra ID&accountName=user@company.onmicrosoft.com
After Encoding
secrets://BeyondTrust%20Password%20Safe/systemName%3DMicrosoft%20Entra%20ID%26accountName%3Duser%40company.onmicrosoft.com
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
Secure#456, but the complete value required by the secret field isapp1-dev@Secure#456then the secret path expression will be as follows to add the required prefix:secrets://BeyondTrust%20Password%20Safe/systemName%3DMicrosoft%20Entra%20ID%26accountName%3Duser%40company.onmicrosoft.com?prefix=app1-dev%40
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
app1-dev, but the complete value required by the secret field isapp1-dev@Secure#456then the secret path expression will be as follows to add the required suffix:secrets://BeyondTrust%20Password%20Safe/systemName%3DMicrosoft%20Entra%20ID%26accountName%3Duser%40company.onmicrosoft.com?suffix=%40Secure%23456
For more information on how to configure the CyberArk Central Credential Provider (CCP), refer to CyberArk Central Credential Provider (CCP).
Path syntax – {params required to fetch secret}/{secretKey}
Secret URL – secrets://{CyberArk Central Credential Provider Source Name}/{params required to fetch secret}/{secretKey}
Important
The URL path should always start with the prefix, secrets://. Each URL should be URL-encoded. Each URL attribute in the path is case-sensitive
The CyberArk Central Credential Provider fetches secret using REST API. The REST API URL format to fetch secrets is as follows:
https://<IIS_Server_Host_URL>/<WebService_NAME>/api/Accounts?<param1>=<value>&<param2>=<value>&
Note
In the provided example, the parameters required to fetch the secret are <param1>=<value>&<param2>=<value>&
Secret URL example:
Before Encoding
secrets://<CyberArk Central Credential Provider Source>/<Object=Cloud Service-AWS-Salesforce-admin&AppID=Test1>/<Content>
Where:
-
<CyberArk Central Credential Provider Source>– Configured Credential Provider -
<Object=Cloud Service-AWS-Salesforce-harshaladmin&AppID=Test1>– Parameters required to fetch secrets -
<Content>– Key to retrieve from the secret response
After Encoding
secrets://CyberArk%20Central%20Credential%20Provider%20Source/Object%3DCloud%20Service-AWS-Salesforce-admin%26AppID%3DTest1/Content
Tip
Use urlencoder.org to encode your URL attributes.
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://CyberArk%20Central%20Credential%20Provider%20Source/Object%3DCloud%20Service-AWS-Salesforce-admin%26AppID%3DTest1/Content?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
localadministrator, but the complete value required by the secret field islocaladminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://CyberArk%20Central%20Credential%20Provider%20Source/Object%3DCloud%20Service-AWS-Salesforce-admin%26AppID%3DTest1/Content?prefix=suffix=%40sp.com
Important
All input parameters must be encoded.
For more information, refer to Retrieve a secret in the CyberArk documentation.
For information on how to configure the CyberArk Conjur Cloud credential provider, refer to CyberArk Conjur Cloud Credential Provider.
Note
The linked document is not maintained by SailPoint and is subject to change without notice.
Path syntax: secrets://{CredentialProviderSourceName}/{ResourceIdOfSecret}
Note
The ResourceIdofSecret attribute can be obtained from Conjur Cloud > Resources then select the created Secret.
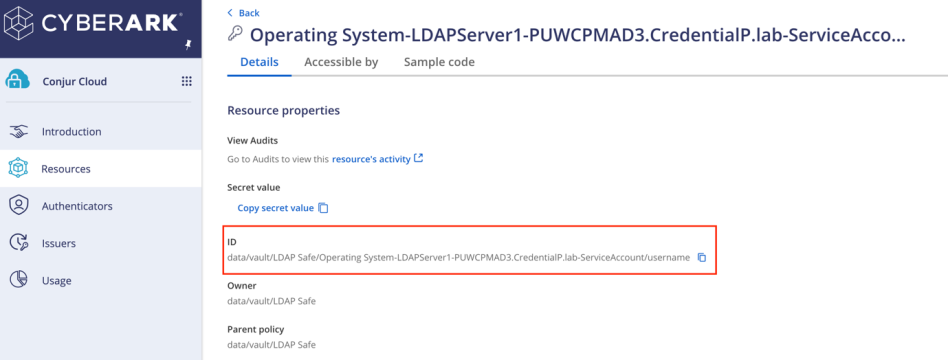
For example:
Before Encoding
secrets://CyberarkConjurCloudSource/data/vault/LDAP Safe/Operating System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount/username
Important
The URL path should always start with the prefix, secrets://. Each URL attribute should be URL-encoded. For example, CredentialProviderSourceName, ResourceIdOfSecret, the prefix, and the suffix must be encoded separately. Each URL attribute in the path is case-sensitive.
After Encoding
After you encode the URL path, it should appear as follows:
secrets://CyberarkConjurCloudSource/data%2Fvault%2FLDAP%20Safe%2FOperating%20System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount%2Fusername
The following is an explanation of the attributes of this URL:
-
CyberarkConjurCloudSource– The Configured Credential Provider in the Credential Provider Section. -
data%2Fvault%2FLDAP%20Safe%2FOperating%20System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount%2Fusername– The encoded resource ID of the secret.
Tip
Use urlencoder.org to encode your URL attributes.
Path syntax: secrets://{CredentialProviderSourceName}/{ResourceIdOfSecret}
For example:
Before Encoding
secrets://CyberarkConjurCloudSource/data/vault/LDAP Safe/Operating System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount/password
Important
The URL path should always start with the prefix, secrets://. Each URL attribute should be URL-encoded. For example, CredentialProviderSourceName, ResourceIdOfSecret, the prefix, and the suffix must be encoded separately. Each URL attribute in the path is case-sensitive.
After Encoding
After you encode the URL path, it should appear as follows:
secrets://CyberarkConjurCloudSource/data%2Fvault%2FLDAP%20Safe%2FOperating%20System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount%2Fpassword
The following is an explanation of the components of this URL:
-
CyberarkConjurCloudSource– Configured Credential Provider in the Credential Provider Section. -
data%2Fvault%2FLDAP%20Safe%2FOperating%20System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount%2Fusername– The encoded resource ID of the secret.
Tip
Use urlencoder.org to encode your URL attributes.
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://CyberarkConjurCloudSource/data%2Fvault%2FLDAP%20Safe%2FOperating%20System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount%2Fusername?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
localadministrator, but the complete value required by the secret field islocaladminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://CyberarkConjurCloudSource/data%2Fvault%2FLDAP%20Safe%2FOperating%20System-LDAPServer1-PUWCPMAD3.CredentialP.lab-ServiceAccount%2Fusername?suffix=%40sp.com
Important
All input parameters must be encoded.
For information on how to configure the Delinea Secret Server (Cloud) – Secrets Manager credential provider, refer to Delinea Secret Server (Cloud) – Secrets Manager.
Path syntax: {Folder_path}/{secretKey}
Before Encoding
Using Folder Name:
secrets://delinea-vault/folder1/cred/applicationName/directoryName/Username
Important
The URL path should always start with the prefix, secrets://. Each part of the URL should be URL-encoded. Each URL attribute in the path is case-sensitive
After Encoding
After you encode the URL path, it should appear as follows:
Using Folder Name:
secrets://delinea-vault/folder1%2Fcred%2FapplicationName%2FdirectoryName/Username
The following is an explanation of the attributes of this URL:
-
delinea-vault– Configured Credential Provider in the Credential Provider Section -
folder1%2Fcred%2FapplicationName%2FdirectoryName– Folder path -
Username– Secret Key which needs to be fetched from the Delinea Secret Server (Cloud) - Secrets Manager.
Tip
Use urlencoder.org to encode your URL attributes.
Path syntax: {Folder_path}/{secretKey}
Before Encoding
Using Folder Name:
secrets://delinea-vault/folder1/cred/applicationName/directoryName/Password
Important
The URL path should always start with the prefix, secrets://. Each part of the URL should be URL-encoded. Each URL attribute in the path is case-sensitive
After Encoding
After you encode the URL path, it should appear as follows:
Using Folder Name:
secrets://delinea-vault/folder1%2Fcred%2FapplicationName%2FdirectoryName/Password
The following is an explanation of the attributes of this URL:
-
delinea-vault– Configured Credential Provider in the Credential Provider Section -
folder1%2Fcred%2FapplicationName%2FdirectoryName– Folder path -
Password– Secret Key which needs to be fetched from the Delinea Secret Server (Cloud) - Secrets Manager.
Tip
Use urlencoder.org to encode your URL attributes.
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is LocalAdmin, but the complete value required by the secret field is
DomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://delinea-vault/folder1%2Fcred%2FapplicationName%2FdirectoryName/Username?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is localadministrator, but the complete value required by the secret field is
localadminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://delinea-vault/folder1 %2Fcred%2FapplicationName%2FdirectoryName/Username?suffix=%40sp.com
-
To add a prefix and suffix –
?prefix=<prefix>& suffix=<suffix>For example, if the secret value returned after evaluation is LocalAdmin, but the complete value required by the secret field is
DomainOne\LocalAdmin@sp.comthen the secret path expression will be as follows to add the required prefix and suffix:secrets://delinea-vault/folder1 %2Fcred%2FapplicationName%2FdirectoryName/Username?prefix=DomainOne%5C&suffix=%40sp.com
Important
All input parameters must be encoded.
Standard format for credential path
secrets://{vault-name}/{folder path}/{secretKey}?prefix=someValue&suffix=someValue2
Note
The prefix and suffix are optional.
For information on how to configure the Delinea Secret Server (On-Premise) – Secrets Manager credential provider, refer to Delinea Secret Server (On-Premise) – Secrets Manager.
Path syntax: {Folder_path}/{secretKey}
Before Encoding
Using Folder Name:
secrets://delinea-vault/folder1/cred/applicationName/directoryName/Username
Important
The URL path should always start with the prefix, secrets://. Each part of the URL should be URL-encoded. Each URL attribute in the path is case-sensitive
After Encoding
After you encode the URL path, it should appear as follows:
Using Folder Name:
secrets://delinea-vault/folder1%2Fcred%2FapplicationName%2FdirectoryName/Username
The following is an explanation of the attributes of this URL:
-
delinea-vault– Configured Credential Provider in the Credential Provider Section -
folder1%2Fcred%2FapplicationName%2FdirectoryName– Folder path -
Username– Secret Key which needs to be fetched from the Delinea Secret Server (On-Premise) - Secrets Manager.
Tip
Use urlencoder.org to encode your URL attributes.
Path syntax: {Folder_path}/{secretKey}
Before Encoding
Using Folder Name:
secrets://delinea-vault/folder1/cred/applicationName/directoryName/Password
Important
The URL path should always start with the prefix, secrets://. Each part of the URL should be URL-encoded. Each URL attribute in the path is case-sensitive
After Encoding
After you encode the URL path, it should appear as follows:
Using Folder Name:
secrets://delinea-vault/folder1%2Fcred%2FapplicationName%2FdirectoryName/Password
The following is an explanation of the attributes of this URL:
-
delinea-vault– Configured Credential Provider in the Credential Provider Section -
folder1%2Fcred%2FapplicationName%2FdirectoryName– Folder path -
Password– Secret Key which needs to be fetched from the Delinea Secret Server (On-Premise) - Secrets Manager.
Tip
Use urlencoder.org to encode your URL attributes.
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is LocalAdmin, but the complete value required by the secret field is
DomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://delinea-vault/folder1%2Fcred%2FapplicationName%2FdirectoryName/Username?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is localadministrator, but the complete value required by the secret field is
localadminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://delinea-vault/folder1 %2Fcred%2FapplicationName%2FdirectoryName/Username?suffix=%40sp.com
-
To add a prefix and suffix –
?prefix=<prefix>& suffix=<suffix>For example, if the secret value returned after evaluation is LocalAdmin, but the complete value required by the secret field is
DomainOne\LocalAdmin@sp.comthen the secret path expression will be as follows to add the required prefix and suffix:secrets://delinea-vault/folder1 %2Fcred%2FapplicationName%2FdirectoryName/Username?prefix=DomainOne%5C&suffix=%40sp.com
Important
All input parameters must be encoded.
Standard format for credential path
secrets://{vault-name}/{folder path}/{secretKey}?prefix=someValue&suffix=someValue2
Note
The prefix and suffix are optional.
For information on how to configure the HashiCorp Vault (Cloud) credential provider, refer to HashiCorp Vault (Cloud) Credential Provider.
Use the path expressions listed in this topic to use the HashiCorp Vault (Cloud) credential provider in your source authentication configurations.
Path syntax – {path_to_secret}/{secretKey}
Secret URL – secrets://{HashiCorp_Source_Name}/{path_to_secret}/{secretKey}
Important
The URL path should always start with the prefix, secrets://. Each URL should also be URL-encoded. Each URL attribute in the path is case-sensitive.
HashiCorp Vault (Cloud) supports static and dynamic secrets. Configure the required secret engines in the HashiCorp Vault (Cloud) server and provide their secret paths in the source.
-
Go to the your HashiCorp secret engine's API document and locate the Get or Generate Credentials API section.
-
Configure the API path to get credentials
Note
Everything after the API version in the URL should be used in place of
<path to secret>.For example, the if URL to fetch secrets is as follows:
http://<vault host>/v1/azure/creds/my-role
Then the
<path to secret>is as follows:azure/creds/my-role
-
Define the key whose value needs to be read from the getCredentials API response for the
<secretKey>.For example, consider the API response for getCredentials as follows:
Copy{
"data": {
"client_id": "408bf248-dd4e-4be5-919a-7f6207a307ab",
"client_secret": "9PfdaDP9qcf98ggw8WSttfVreFcN4q9c4m4x",
...
}
}If the secret expression wants the Client ID field from the connector source, then
<secretKey>should be set toclient_id.
Secret URL example:
Before Encoding
secrets://<HashiCorp Source>/<mysecret/Admin User>/<Admin username>
Where:
-
<HashiCorp Source>– Configured Credential Provider in the Credential Provider Section -
<mysecret/Admin User>– Path to the secret -
<Admin username>– Key to retrieve from the secret path
After Encoding
secrets://HashiCorp%20Source/mysecret%2FAdmin%20User/Admin%20username
Tip
Use urlencoder.org to encode your URL attributes.
Note
By default, the HashiCorp Vault (Cloud) cred ential provider checks the {secretKey} in response to the following paths by default:
-
$. -
$.data -
$.data.data
If any getCredentials API response returns {secretKey} from another path, then add the following entry key into the HashiCorp source XML for all those paths:
<entry key="secretPaths" value="path1,path2"/>
For example:
<entry key="secretPaths" value="data.data.data,data.path1"/>
For more information on SailPoint's REST APIs, refer to Best Practices: REST API Authentication and REST API - Update Source (Partial) in the SailPoint Developer Community.
You can fetch secrets from the K/V version2 engine. For more information, refer to Read secret version in the KV secrets engine - version 2 (API) section of the HashiCorp developer documentation.
Note
The linked document is not maintained by SailPoint and is subject to change without notice.
Path syntax – {secret-mount-path/data/path to secret}/{secretKey}{?version=<versionNumber>}
For example:
Before Encoding
secrets://HashiCorp Source/StaticSecrets-v2/data/Active Directory/PASSWORD/Pass word
After Encoding
secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSWORD/Pass%20word
Where:
-
HashiCorp Source– Configured Credential Provider in the Credential Provider Section -
StaticSecrets-v2–secret-mount-path -
Active Directory/PASSOWRD– Path to the secret -
Pass word– Key to retrieve from the secret path
Read Secret with version number example, after encoding:
secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSOWRD/Pass%20word?version=3
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSWORD/Pass%20word?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
localadministrator, but the complete value required by the secret field islocaladminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSWORD/Pass%20word?suffix=%40sp.com
Important
All input parameters must be encoded.
For information on how to configure the HashiCorp Vault (On-Premise) credential provider, refer to HashiCorp Vault (On-Premise) Credential Provider.
Path syntax – {path_to_secret}/{secretKey}
Secret URL – secrets://{HashiCorp_Source_Name}/{path_to_secret}/{secretKey}
Important
The URL path should always start with the prefix, secrets://. Each URL should also be URL-encoded. Each URL attribute in the path is case-sensitive.
HashiCorp Vault (On-Premise) supports static and dynamic secrets. Configure the required secret engines in the HashiCorp Vault (On-Premise) server and provide their secret paths in the source.
-
Go to the your HashiCorp secret engine's API document and locate the Get or Generate Credentials API section.
-
Configure the API path to get credentials
Note
Everything after the API version in the URL should be used in place of
<path to secret>.For example, the if URL to fetch secrets is as follows:
http://<vault host>/v1/azure/creds/my-role
Then the
<path to secret>is as follows:azure/creds/my-role
-
Define the key whose value needs to be read from the getCredentials API response for the
<secretKey>.For example, consider the API response for getCredentials as follows:
Copy{
"data": {
"client_id": "408bf248-dd4e-4be5-919a-7f6207a307ab",
"client_secret": "9PfdaDP9qcf98ggw8WSttfVreFcN4q9c4m4x",
...
}
}If the secret expression wants the Client ID field from the connector source, then
<secretKey>should be set toclient_id.
Secret URL example:
Before Encoding
secrets://<HashiCorp Source>/<mysecret/Admin User>/<Admin username>
Where:
-
<HashiCorp Source>– Configured Credential Provider in the Credential Provider Section -
<mysecret/Admin User>– Path to the secret -
<Admin username>– Key to retrieve from the secret path
After Encoding
secrets://HashiCorp%20Source/mysecret%2FAdmin%20User/Admin%20username
Tip
Use urlencoder.org to encode your URL attributes.
Note
By default, the HashiCorp Vault (On-Premise) credential provider checks the {secretKey} in response to the following paths by default:
-
$. -
$.data -
$.data.data
If any getCredentials API response returns {secretKey} from another path, then add the following entry key into the HashiCorp source XML for all those paths:
<entry key="secretPaths" value="path1,path2"/>
For example:
<entry key="secretPaths" value="data.data.data,data.path1"/>
For more information on SailPoint's REST APIs, refer to Best Practices: REST API Authentication and REST API - Update Source (Partial) in the SailPoint Developer Community.
You can fetch secrets from the K/V version2 engine. For more information, refer to Read secret version in the KV secrets engine - version 2 (API) section of the HashiCorp developer documentation.
Note
The linked document is not maintained by SailPoint and is subject to change without notice.
Path syntax – {secret-mount-path/data/path to secret}/{secretKey}{?version=<versionNumber>}
For example:
Before Encoding
secrets://HashiCorp Source/StaticSecrets-v2/data/Active Directory/PASSWORD/Pass word
After Encoding
secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSWORD/Pass%20word
Where:
-
HashiCorp Source– Configured Credential Provider in the Credential Provider Section -
StaticSecrets-v2–secret-mount-path -
Active Directory/PASSOWRD– Path to the secret -
Pass word– Key to retrieve from the secret path
Read Secret with version number example, after encoding:
secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSOWRD/Pass%20word?version=3
If any secret paths have a prefix or a suffix, you must append a query parameter to the secret path as follows:
-
To add a prefix –
?prefix=<prefix>For example, if the secret value returned after evaluation is
LocalAdmin, but the complete value required by the secret field isDomainOne\LocalAdminthen the secret path expression will be as follows to add the required prefix:secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSWORD/Pass%20word?prefix=DomainOne%5C
-
To add a suffix –
?suffix=<suffix>For example, if the secret value returned after evaluation is
localadministrator, but the complete value required by the secret field islocaladminstrator@sp.comthen the secret path expression will be as follows to add the required suffix:secrets://HashiCorp%20Source/StaticSecrets-v2%2Fdata%2FActive%20Directory%2FPASSWORD/Pass%20word?suffix=%40sp.com
Important
All input parameters must be encoded.